Papers
The Security Solutions for pipelines and Remote Installations
The Security Dilemma:
The motives for terrorist attacks are often unclear. This was the case in Algeria earlier this year when the Ain Amenas gas plant was attacked. Al-Qaeda in the Islamic Maghreb (AQIM) had run short of funds after paying for the conflict in neighbouring Mali. Amenas was relatively unprotected, extremely remote with the potential to extract a high price from the oil companies BP and Statoil.
Lucrative oil and gas exploration has often been conducted in remote areas with limited security infrastructure. The deadly attack on Ain Amenas gas complex will do little to discourage the drive for lucrative energy exploration in northern Africa and the Gulf, however oil companies shall be forced now to increase personnel and physical security after largely ignoring the risks of operating in the remote desert region. The risks are never going to outweigh the rewards from working in these environments.
In the wake of this, energy companies will have to study their operations for possible flaws and upgrade their contingency plans with information gleaned from the attack.
It is clear that well-guarded permanent facilities with visible deterrence and physical security are less likely to be attacked vulnerable than pipelines or remote temporary exploration facilities. Therefore security solutions for pipelines and remote facilities will become more and more prevalent in the marketplace.
Pipeline Security:
Pipelines offer a complex linear security challenge and are of particular concern in the MENA region. They are often in the most remote areas extending over hundreds, if not thousands, of miles. When a pipeline is damaged significant revenues will be lost, damage is caused to the local environment and the leakage is a potential hazard to the local population and wildlife. Often the damage is not apparent to the pipeline operator for weeks and often it takes days to accurately pinpoint the location of the damage.

Figure 1: The challenge of pipeline security
Oil & gas producers and pipeline operating companies appreciate the consequences of attacks on pipeline networks; however few have managed to teach personnel ‘on the ground’ how to identify vulnerable network locations and recognise methods of target assessment and attack from the perspective of the total pipeline network.

Figure 2: Where to Look
The terrorist groups are mobile and the required area to cover is huge and impossible to police with patrols. These small, agile groups have the element of surprise. Therefore the security solution deployed needs to fully understand the mechanism of the threat and how to mitigate it. The counter needs to be rapidly deployable and agile.
"Think like the terrorist"

Figure 3: Understanding the complexities and behaviour of the threat
The first key concept of a Security Solution program is to ‘Think Like The Terrorist.’ Once we understand the terrorist, the potential motives, we can begin to manage, respond and act in a manner that accounts for the complexity of his behavior. All security personnel will need to think like terrorists to fully master the function and integration of the security solution.
AIS Security Solutions provide robust surveillance and protection of these key assets using a wide range of solutions including:
Security & Protection Measures:
Training is required to:
- understand the critical processes and security challenges
- Identify vulnerable locations and key assets by learning how to recognise methods of target assessment and attack.
- Recognise terrorist preferencing in target assessment & attack methodologies – “Think like the Terrorist”
- Plan and conduct effective pipeline inspections to deter and detect intrusions (on land, mounted/dismounted, air, satellite)
- Create a workable inspection plan.
- Design and develop specialised incident location search techniques
- Document and develop a comprehensive Incident Scene Database
- Analyse incident information using to forecast potential incident locations and terrorist attack methodologies.
- Develop Standard Operating Procedures (SOPs) for Security personnel.
Security & Protection Measures:

Figure 4 – Common Operational Picture of Pipeline Security
Systems for protection must have a high probability of detection with a very low probability of false alarm activations but with pipelines, the ability to pinpoint the location of any incident is also a vital requirement if loss is to be avoided or minimized.
Solutions for protection of pipelines exist that are agile, can be rapidly deployed and can provide a high degree of protection to pipelines and terminals. These can be networked and interfaced with other sensors into a Common Operational Picture (COP) providing Total Domain Awareness (TDA) over the whole infrastructure.
Within the last 10 years, effective and reliable technologies for pipeline surveillance have entered the market. With a clear understanding of how these can be integrated into a wider security solution, security integrators (such as AIS Security Solutions) have the ability to provide the degree of protection required by pipeline operators. With advances in:
- Miniaturised sensors, embedded and on-surface – seismic & acoustic
- Standardised data-processing techniques
- Remote Communications technology deterrence and reaction is now possible

Figure 5 - Embedded Robust Sensors on Pipeline
Combining the most robust underground (buried) systems and over-ground (exposed) systems suitably shall provide the degree of protection required offering deterrence and detection, recognition and detection of threat. Furthermore active methods for dissemination of the information to the fast-response teams will be vital to ensure follow through.Security Integration with Supervisory Control and Data-Acquisition (SCADA)
SCADA Systems manage vital infrastructure and processes. AIS Security Systems, working with our partner, Orion Systems (www.orionsystems.com) offers standardised, modular SCADA system for monitoring and controlling gas and oil pipelines and other utilities. Designed to manage infrastructure, our SCADA system uses a software platform that provides realtime control, optimises exploitation management systems and forms the backbone of a command, control and intelligence centre.
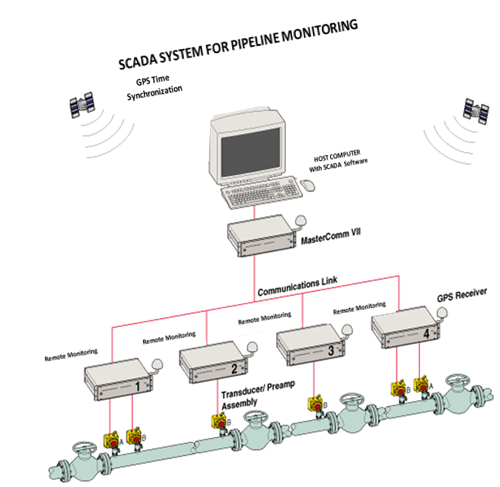
Figure 6 - SCADA Solution for Pipeline Monitoring
Our solution offer secure encryption to protect data over SCADA communication links, which is vital for critical infrastructure to be properly protected
The modular structure of our SCADA solution facilitates adaptability for both standard tasks and and special demands. This modularity also assures easy expansion for higher functions, such as diagnostics, simulation, and optimisation. These functions are easily integrated within the system on demand.
AIS Security Solutions – an Effective Security Shield
AIS Security Solutions provides the complete security protection combining electronic and physical security and deterrence with the active measures to prevent further attack - an Effective Security Shield. Our solutions for pipeline protection are designed to protect Gas, Oil and Liquid Pipelines and other utility pipeline distribution networks.






















